
Security-Enhanced Linux (SELinux) is a security architecture for Linux systems that allows administrators to have more control over who can access the system. It was originally developed by the United States National Security Agency (NSA) as a series of patches to the Linux kernel using Linux Security Modules (LSM). In Linux, file permissions have been the method of securing Linux systems. But in most cases, file permissions are just not enough. Therefore, SELinux was invented. Explore how to setup SELinux on a Linux server.
Please refer to the following guides for information: How to locate directory file context and restore it with SELinux, and other related guides such as how to create and deliver a report based on system utilization on a Linux-based OS and how to install Static pods in Kubernetes and how to use container insights to get the full benefits of Azure Monitor for Azure Kubernetes workload.
SELinux (Security-Enhanced Linux) provides access control to a Linux server, where every system call is denied unless it has been allowed. I will critically explain how to use SELinux to make sure that serious security incidents will never happen on your server/Infrastructure.NOTE: If SELinux is enabled and nothing else has been configured, all system calls are denied.
SELinux keywords needed for setup on a Linux server
– Policy – A collection of rules that define which source has access to which target.
– Source domain – The object that is trying to access a target. (A user or process)
– Target domain – The object that a source domain is trying to access. (A file or port?
– Context – A security label that is used to categorize objects in SELinux.
– Rule – A specific part of the policy that determines which source domain has which access permissions to which target domain.
– Labels – Same as context label, defined to determine which source domain has mandatory access control to which target domain.
SELinux can be in 3 Modes. Enforcing, permissive and disabled. If you disable SELinux, no SELinux activity will be happening at all, but if you enable SELinux, you can select to put SELinux in enforcing mode or in permissive mode. In enforcing mode, SELinux is fully operational and enforcing all SELinux rules in the policy. If SELinux is in permissive mode, it logs all SELinux related activity, but doesn’t block access.
SETTING UP SELINUX ON A LINUX SERVER
To set the default SELinux mode while booting, use the file /etc/sysconfig/selinux.

On a server that currently has SELinux enabled, you can use the getenforce command to see whether it is currently in enforcing or in permissive mode. To switch between permissive and enforcing mode, you can use setenforce . The command setenforce 0 puts SELinux in permissive mode, and setenforce 1 puts SELinux in enforcing mode.
Another useful command is sestatus . If used with the option -v , this command shows detailed information about the current status of SELinux on a server.
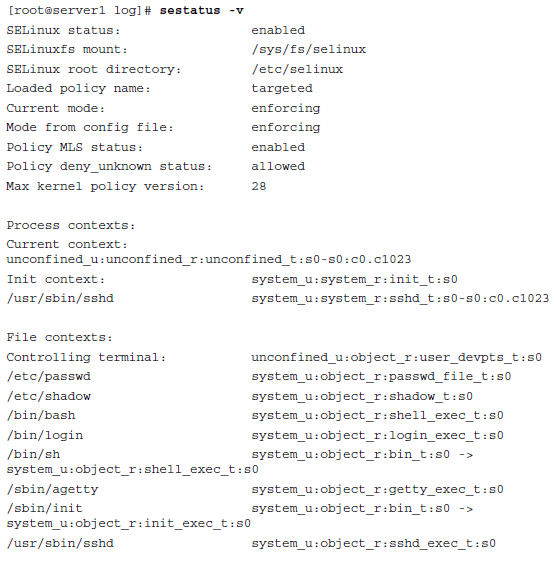
Hope this was helpful in setting up and checking basic SELinux configurations. We guess you have insight on how to setup SELinux on a Linux server.
