
A brief history of Trellix will be vital before proceeding. McAfee Enterprise and FireEye merged as a new company under the name Trellix. Sometime in June 2021, FireEye sold its name and products business to Symphony Technology Group (STG). STG combined FireEye with its acquisition of McAfee’s enterprise business to launch Trellix, an extended detection and response (XDR) company. In this article, we will show you how to resolve and prevent this issue: Windows Defender detects Endpoint Security HipHandlers.dll. Please see How to update Microsoft Defender Antivirus into the install image of Windows.
Microsoft continually updates security intelligence in antimalware products to cover the latest threats and to constantly tweak detection logic, enhancing the ability of Microsoft Defender Antivirus and other Microsoft antimalware solutions to accurately identify threats.
Here are some more exciting articles: How to Disable Data Execution Prevention and determine that hardware DEP is available and configured, How to enable or disable Microsoft Edge from showing Web Content via Local Group Policy Editor, and how to Manage Windows Defender Antivirus Through Microsoft Endpoint Manager Admin Dashboard and Intune.
What is hiphandlers.dll?
The hiphandlers.dll is part of Trillix Host Intrusion Prevention. According to the hiphandlers.dll version information. This file has the description HIPS Signatures most of the time and the library can be loaded and executed in any running process.
The root cause for Windows Defender detecting”Endpoint Security HipHandlers.dll”
This occurs during the installation of Trellix Endpoint Security (ENS) or an Exploit Prevention content update.
During this time, Windows Defender might incorrectly detect and delete the Exploit Prevention content file HIPHandlers.dll or HIPHandlers64.dll as a malicious file. The detection name according to Trillix is “HackTool:Win32/Mimikatz“.
Note: In the context of an ENS Threat Prevention installation, this detection can result in an installation failure.
If the issue occurs during an Exploit Prevention content update, the Windows Event Log contains a Windows Defender event similar to the example below. Please dismiss this Windows security notification as the file was incorrectly flagged as stated by Trellix.

Please see Workaround for Microsoft Support Diagnostic Tool Vulnerability, and Pleasant User Group Permission and User Access.
The solution to Endpoint Security HipHandlers.dll detection
Windows Defender’s older virus definitions versions result in the detection of these files. Please see How to remove the Microsoft Defender update on Windows 10 and Windows Server image.
You must update the Windows Defender security intelligence content to the latest version available from Microsoft. Depending on your enterprise architecture and the scope of impacted systems, there are several ways to deploy the latest version.
To clear the current cache and trigger an update, use the following commands below as an administrator. Please see Windows Security Intelligence Update: How to clear Cache and Manually Update Microsoft Defender.
cd %ProgramFiles%\Windows Defender
MpCmdRun.exe -removedefinitions -dynamicsignatures
MpCmdRun.exe -SignatureUpdate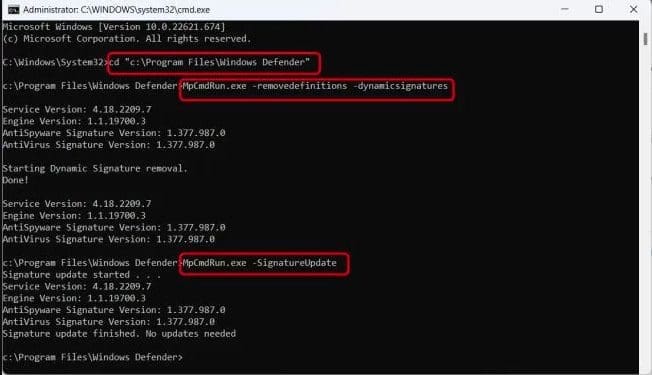
Note: To help ensure your antimalware solution detects the latest threats, get updates automatically as part of Windows Update.
I hope you found this blog post helpful on Windows Defender Detects Endpoint Security HipHandlers.dll. Please let me know in the comment section if you have any questions.
