Delegate control for BitLocker recovery keys in Active Directory

Active Directory (AD) delegation is a critical part of security and compliance. By delegating control overactive directory, you can grant users or groups the permissions they need without adding users to privileged groups like Domain Admins, etc. Please see how to clear the TPM via the management console or Windows Defender Center App, how to deploy Microsoft BitLocker Administration and Monitoring Tool, and how to uninstall your current version of MBAM and run setup again.
You can use organizational units (OUs) to delegate the administration of objects, such as users or computers, within the OU to a designated individual or group.
To delegate administration by using an OU, place the individual or group to which you are delegating administrative rights into a group, place the set of objects to be controlled into an OU, and then delegate administrative tasks for the OU to that group.
Here are some interesting guides: How to enable or disable BitLocker Drive Encryption on Windows 10 and Virtual Machines, and how to clear, enable or disable TPM in Windows via the BIOS or UEFI.
Active Directory Domain Services (AD DS)
Active Directory Domain Services (AD DS) enables you to control the administrative tasks that can be delegated at a very detailed level. For example, you can assign one group to have full control of all objects in an OU; assign another group the rights only to create, delete, and manage user accounts in the OU; and then assign the third group the right only to reset user account passwords.
You can make these permissions inheritable so that they apply to any OUs that are placed in subtrees of the original OU.
Kindly visit this guide to learn more on how to fix the missing BitLocker Recovery Tab in Active Directory Users and Computers. Also, see how to backup existing and new BitLocker recovery keys to Active Directory.
When BitLocker keys are configured to be stored in AD. This requires that BitLocker Drive Encryption Administration Utilities be installed on your device and you MUST be a domain Admin to be able to view these keys or have these rights delegated. In this guide, I will be showing you how to delegate control for the BitLocker recovery keys.
Kindly visit these guides s”how to backup existing and new BitLocker recovery keys to Active Directory. Also, see how to backup existing and new BitLocker recovery keys to Active Directory“.
Efficient Delegation Using the Control Wizard for Bitlocker Recovery Keys
Nevertheless, Use the Delegation of Control Wizard to empower support staff without granting unnecessary privileges for Bitlocker recovery keys. Before proceeding, ensure you have a security group or OU that you wish to delegate these rights are present.
Therefore, Open Server Manager, click AD DS on the Dashboard, right-click the Server, and choose Active Directory Users and Computers.
In ADUC (dsa.msc), right-click on the OU that contains your computer objects and select Delegate Control.
Similarly, Click “Next”.
This will open the Delegation of Control wizard. Consequently, Click on Add.
Nonetheless, Add the group you wish to delegate the right to view the BitLocker Recovery Keys. You may want to see this guide for more information “How to backup existing and new BitLocker recovery keys to Active Directory using a simple script“.
In addition, Click “Next” to continue with the configuration
Create a custom task to delegate. Click “Next”.
Only the following objects in the folder: msFVE-REcoveryInformation objects
However, Click “Next”.
Click on “Full Control”. Click “Next” to proceed
Furthermore, Click on Finish to complete the configuration. From henceforth, the members of the group we have added will be able to access the Bitlocker recovery keys stored inside the organizational unit named Support Admin.
Note: These rights above will also grant the delegated Support Agents Full control. This means they can read and delete these keys using the ADSI edit commands. If desired, use the LDP.exe tool to delegate control for Bitlocker recovery keys with proper read rights.
You may want to read “how to restore deleted user accounts in Active Directory with Microsoft LDP and PowerShell“.
Viewing the BitLocker Recovery Keys
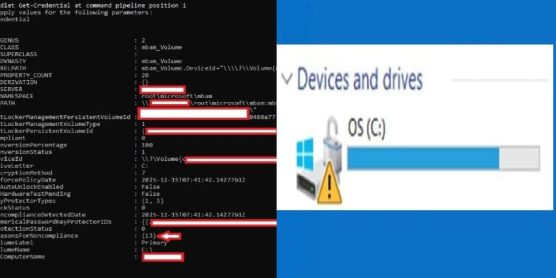
You can use the BitLocker Drive Encryption Administration Utilities. Kindly visit these guides “how to backup existing and new BitLocker recovery keys to Active Directory. Also, see how to backup existing and new BitLocker recovery keys to Active Directory“. This can also be done via PowerShell with the command below.
Get-ADComputer computername | Get-ADObject -pr * | Select-Object distinguishedname, msFVE-REcoveryPassword, whencreatedFAQs
BitLocker protects and prevents a unauthorized users from booting another operating system or run a software hacking tool from breaking Windows file and system protections or performing offline viewing of the files stored on the protected drive. This protection is achieved by encrypting the entire Windows volume. With BitLocker all user and system files are encrypted including the swap and hibernation files.
BitLocker enhances data protection by bringing together two major sub-functions. Full drive encryption and the integrity checking of early boot components. Integrity checking the early boot components helps to ensure that data decryption is performed only if those components appear unmolested and that the encrypted drive is located in the original computer
BitLocker implement integrity checking starting with the boot manager and then continuing to check each subsequent component. The boot manager performs a cryptographic verification of its own integrity before checking the integrity of the next component in the boot process (winload.exe or winresume.exe, if coming from hibernation). Once control is passed to the OS loader, it will check CI.dll, and
once the computer boots, Code Integrity (CI.dll) will perform integrity checks on all other modules.
I trust you discovered valuable insights in this blog post. If you have any queries, please ask in the comment section. Additionally, Your understanding of delegate control for Bitlocker recovery keys matters.