SCVMM setup Error 10421: Fix VMM Service Account conflict
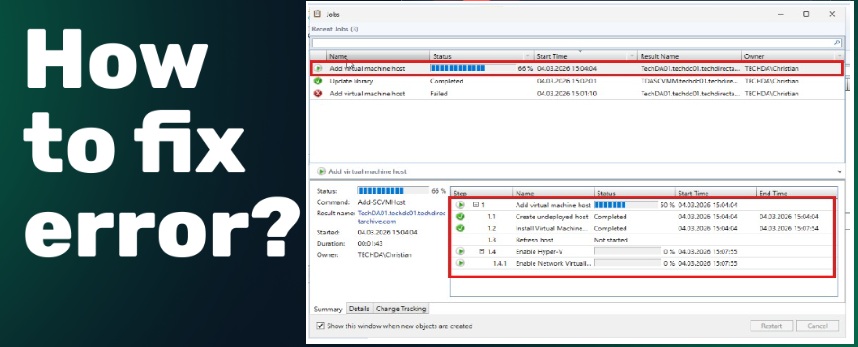
In this article, we shall discuss ‘SCVMM setup Error 10421: Fix VMM Service Account conflict”. System Center Virtual Machine Manager (SCVMM) is part of the System Center suite and helps to provide a unified management experience across on-premises, service provider, and the Azure cloud. Please, see SCVMM setup Fails: Fix Missing Windows ADK Deployment Files,…
Read More “SCVMM setup Error 10421: Fix VMM Service Account conflict” »




![Inbound connection Error: Failed to Perform Scheduled Replication [Part 2]](https://techdirectarchive.com/wp-content/uploads/2026/03/Snapshot-replication-failed.jpg)


![Synchronize Apple Calendar on Windows with Outlook [Part 2]](https://techdirectarchive.com/wp-content/uploads/2026/02/integrate-Icloud-with-Windows.jpg)