How to Secure your API key in Postman

In this article, I will show you how to Configure Postman for a Secure API key Authentication. API “Application Programming Interface” is the bedrock of all system applications. Without an API it will be impossible for the backend logic of an application to communicate with the frontend. Please see How to Import Data from a GitHub Repository to Postman, and “Benefits of Azure API Management and how to create an API instance“.
API also makes it possible for an application to make a call or send a request to another application.
You can further read about How to Integrate Postman With GitHub. Also, see how to use Postman for your POST Request, How to Use Postman with the Amazon Pinpoint API.
One of the many ways to prove your identity and gain access to an API is using an API key. I am going to show you three ways to secure API keys.
1: Do not Hard Code your API keys directly into your code
Instead of hard-coding or embedding your API keys into your code why not store them as variables? Variables work perfectly in decoupling your secrets or API keys from your code. When you store your API key as a variable makes it easier for you to revoke, or refresh the value anytime.
We are going to create an API key as an environment variable that can be used with different collections and can be shared with team members and collaborators.
Open Postman and click on the + icon to create an environment and the environment variable. I name my environment variable api-key. Make sure you save the environment by clicking on the Save button.

On the No environment drop-down by the top right you can select the new environment just created to set as active.
You can also select from Environments in the left sidebar and select the Set active icon next to an environment to make it the active environment.

If the API Key is not supplied or the wrong API Key is added during a request. You will get an Invalid API Key response like the below request.
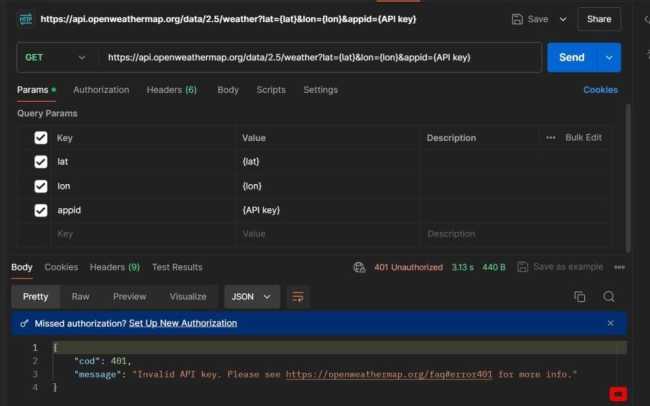
The variable you created earlier can be referenced in text fields with double curly braces, as you can see here in the Params. Hover over the variable name “api-key” to inspect the variable’s value and scope.

Also, see How to use Command-Line on Git Bash and GitHub Desktop to PUSH local code to GitHub, and how to Setup Public Load Balancer in Azure.
2. Do not share your API keys with third-party or your team
If you are sharing the same Postman environment with your team. You will need to keep your Keys safe and private by only updating the current value.
The current value is only local to your Postman app session. Immediately you log out of Postman all the values will disappear and it does not get synced to the account you shared with your team unless you persist the value.

You can also define environment variables by Type. You can change the default type which is plain text to secret which masks the initial and current values. The Secret type is used to prevent the disclosing of sensitive data like API Keys, passwords, and tokens.

3. Use a Place-holder name and not leak your API keys publicly
When generating your API documentation and publishing it publicly, avoid leaking secrets, tokens, or API Keys to the public.
You can use a placeholder text or a dummy value for your API key’s value. The initial value is what will be posted publicly while the current value will remain locally.

When the API Documentation is finally published the key will not be exposed as the image below depicts.

FAQs
It is very important that you keep your API Key safe because once it’s exposed to the public it can lead to unauthorized access to the API and data leaks will occur.
The best way to secure your API keys is to keep them on your personal server where you can securely access them. You can carry out authentication to your server using a JWT.
I hope you found this blog post on how to Secure your API key in Postman Interesting and helpful. If you have any questions do not hesitate to ask in the comment section.