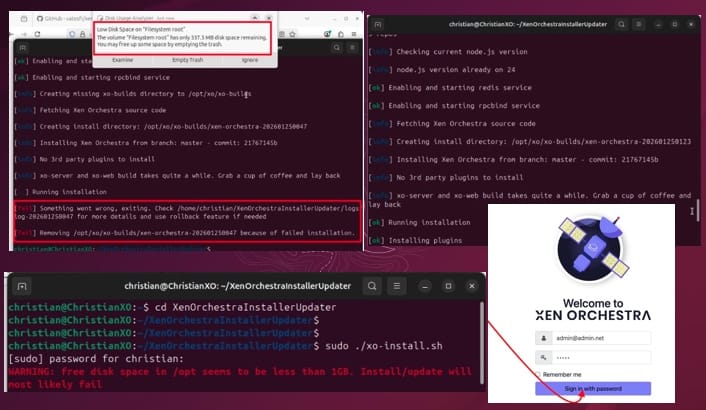
How to block the Change Password Feature for All Users via the Exchange Administrative Center

Now, imagine you don’t want to give this feature to your end-users, or maybe not to all of them. In this case, you have to modify certain settings on the Exchange server side. To do this, you will have to log on to your company’s Exchange Administrative Center with an Exchange Admin account. Using this…