
I recently encountered the error message “The Group Policy settings for BitLocker startup options are in conflict and cannot be applied. Contact your system administrator for more information” during a BitLocker Encryption setup. The issue occurred while attempting to turn on BitLocker encryption through the Control Panel. The group policy setting for BitLocker may cause this error when enabling BitLocker Encryption. To fix it, open the policy and set “Require additional authentication at startup” to “Not Configure.” Please see this guide on how to deploy Microsoft BitLocker Administration and Monitoring Tool
Some Context on BitLocker Encryption with TPM (Trusted Platform Module)
BitLocker Drive Encryption is a data security tool that integrates with the operating system and solves the risks of data theft or disclosure from lost, stolen or improperly discontinued machines.
The TPM is a hardware component that computer makers include in many newer computers. It integrates with BitLocker to help safeguard user data and confirm that a computer has not been tampered with when the system was turned off.
In addition to the TPM, BitLocker provides the option of locking the normal startup process until the user enters a personal identification number (PIN) or inserts an external device, such as a USB flash drive, that carries a startup key.
These extra security features enable multifactor authentication and assurance that the machine will not start or restart from hibernation unless the right PIN or startup key is supplied. If you are having an issue integrating BitLocker with TPM, see how to fix your device cannot use a Trusted Platform Module: Allow BitLocker without a compatible TPM
Learn more about BitLocker encryption: Microsoft Bitlocker Administration and Management: Effect of renaming an MBAM or BitLocker protected Computer, BitLocker System Partition: Detailed steps to troubleshoot and fix System Partition not available or large enough [Part 2],
So, lets see how to solve this problem by changing the BitLocker configuration settings from the Group policy editor.
How to Set Require Additional Authentication at Startup to “Not Configured“
Open the group policy editor by clicking Start or press the Windows key then enter ‘group policy’. Click the ‘Edit group policy’ or press open:

Under “Computer Configuration” follow on the path below.
Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives” - Double click: “Require additional authentication at startup”

Change the following:
- Under Require additional authentication at startup window select “Not Configured”
- Click “Apply” and “OK”

For your changes to take effect, open the command prompt as administrator and execute the following: gpupdate and wait till the computer and group policy update is successfully applied. Or simply restart your system.

Click Start or press the Windows key and search for ‘BitLocker’. Click the ‘Manage BitLocker’ or press open.
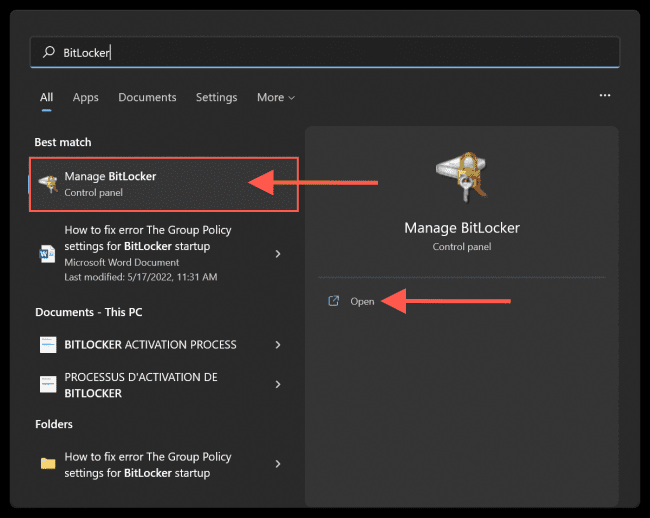
Now continue with the BitLocker Encryption by following this detailed guide on how to enable BitLocker on Windows 10 and virtual machine.
How to Enable Authentication PIN at Windows Startup
If you have successfully enabled BitLocker on your Drive. If you are required to set up an authentication PIN at Windows startup follow the steps below.
- Open the group policy editor.
- Navigate to “Require additional authentication at startup” as shown below.

Change the following:
- Under Require additional authentication at startup select “Enabled”
- Click on the drop-down under “Configure TPM startup PIN” and select “Require startup PIN with TPM”
- Click “Apply” and “OK”

Next, open the Command prompt as administrator then enter
gpupdateEnter the following command to turn on the authentication PIN:
manage-bde -protectors -add C: -TPMAndPIN Replace the C: with your Drive Letter. You will be required to input your preferred PIN twice, then close the terminal.

After this, whenever you power on your system. You will be required to input the set pin to unlock your system drive before booting to Windows.

Please see MBAM Report Errors: Understanding Microsoft BitLocker Administration and Monitoring compliance state and error status and Encryption Algorithm: Why does MBAM not automatically re-encrypt MBAM or Bitlocker protected devices.
I hope you found this blog post on how to fix “The Group Policy settings for BitLocker startup options are in conflict and cannot be applied” helpful. If you have any questions, please let me know in the comment session.
