Request a certificate signing request in Windows using Microsoft Management Console

In this article, we shall discuss how to Request a certificate signing request in Windows using Microsoft Management Console. SSL certificates are what enable websites to move from HTTP to HTTPS, which is more secure. An SSL certificate is a data file hosted in a website’s origin server. See the following interesting guides on how to import a certificate into the Trusted Root and Personal file certificate store, and how to export a certificate in PFX format in Windows.
SSL certificates make SSL/TLS encryption possible, and they contain the website’s public key and the website’s identity, along with related information. Since certificates play a vital role in securing communications between federation servers, claim-aware applications, web clients, etc.
Therefore, AD FS requires a certificate for Secure Socket Layer (SSL) server authentication on each federation server in your federation server farm.
If you are not going to perform the certificate request yourself. You are requested to provide the components needed to create a certificate for you. Also, see Upgrade Windows Admin Center 2306 – 2311: Run WACmg v2401.
Steps for setting and Configuring AD FS
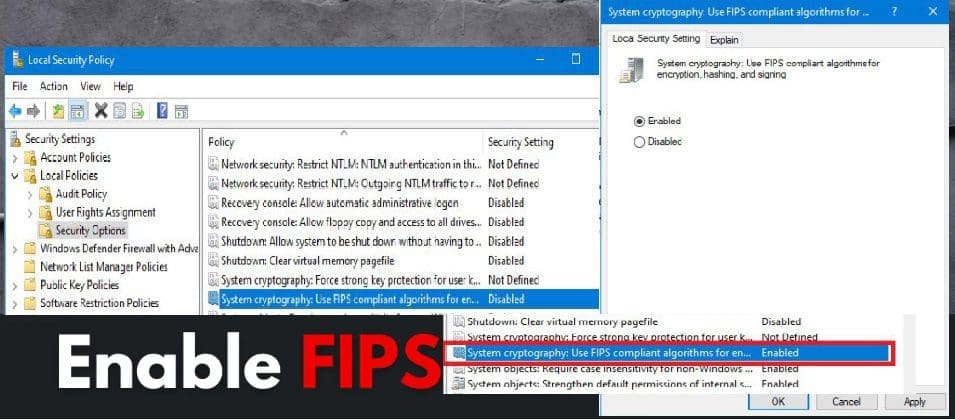
This will need to be replicated to other domain controllers and for safety precautions, DC will have to wait 10 hours from when the key is created to ensure that you are able to answer password-related queries that relate to this key. See this article on deploying ADFS farm.
Note: To avoid AD FS from failing to start, you can run this PowerShell command in advance to ensure you meet the 10 hours requirements. The image below shows the service account being used
Step 1 – Request for a certificate to work with AD FS
See the following AD FS Requirements for more information. Please see Guide on federating ADFS with Azure Active Directory, Log Off: How to sign out of Windows Server 2012, and ADFS: How to install and configure Active Directory Federation Service in Windows Server.
How to Open Certificate Manager
Use the step in the image below to manage certificates. But I prefer using the alternative method described below in creating certificates. Here I can specify the right snap-in type of users and computers to be managed.
- Click the Start button,
- Type certmgr.msc in the search field, and
- Click the Enter key
Search for run, type certmgr.msc in the open field and press enter. This step will open the local computer certificate management console.
Alternatively, this can be accessed using the MMCClick the Start button, type mmc in the search field, and click the Enter key
Or search for run, type mmc in the open field and press enter.Launch the MMC console
Note: In using the MMC Console, you will have to add the certificate snap-in as shown below.
Click on file, select add/remove Snap-in
Select Certificate and click on add
Select the local computer and click on finish
Note: You can also run this on another computer. Finally, click on okay.
This will certificate management console. Expand the certificates, you will have access to all folders in the local computer as shown below.
Also, see how to save and stop modification to Microsoft Management Console, and Linux: How can I tell if a password is set for a user account, and How to Disable Driver Signature Enforcement in Windows 11.
Step 2: Create a Custom Request
In order to create a certificate signing request, follow the steps below. Click on Personal, select all tasks, and advanced options and Create a Custom Request
Click on Next
Select proceed without enrolment

On the Custom request, leave everything as default.
On the Certificate Information page, expand the details tab as shown below and click on properties.
Enter your desired friendly name and description and click on apply
On the Subject menu, enter the relevant details and click on Apply.
Here: I selected the CN and entered the field
- Under Alternative Name, I entered the same values as the CN as required by ADFS.
- I also entered under DNS the Subject alternate name
- Also entered certauth.domain.de to support authentication on port 443.
- And lastly, I ensured the SAN contained “enterpriseregistration.<upn suffix> for more information
On the Private Key Menu, expand the key option in order to select your desired key size.
When you are done, click on ok and this will display the Certificate Information Window once more
Click on next. Finally, enter your desired path to store the certificate. Remember to add the .req to the filename
Click on finish. See this guide on how to import the certificate to the Trusted Root and Personal File Certificate Store.
Note: Self-signed certificates are not trusted by default and they can be difficult to maintain. Also, they may use outdated hash and cipher suites that may not be strong. For better security, purchase a certificate signed by a well-known certificate authority.
FAQs on creating a certificate signing request in Windows
The choice of the public key algorithm in a CSR is crucial for security. Common options include RSA and ECC (Elliptic Curve Cryptography). The selection can impact the certificate’s security and compatibility with various systems. RSA is widely supported, while ECC offers similar security with shorter key lengths. The choice should align with your security requirements and the compatibility of systems where the certificate will be used
After creating a CSR, the next step is to submit it to a trusted Certificate Authority (CA). The CA will review the CSR, verify the information, and issue a digital certificate if the request is valid. Once you receive the certificate from the CA, you can install it on your server for secure communication.
I hope you found this blog post helpful on how to Request a certificate signing request in Windows using Microsoft Management Console. If you have any questions, please let me know in the comment session.